Application Whitelisting & Blacklisting
By Hash and/or Location
See “mandos” in action for yourself
What’s happening?
Before applying the compliance rules, any applications can run from any location.
But once the compliance rules are applied, applications are restricted from running based on their directory location, and their hash.
What else can it do?
- log application execution to syslog for an audit trail.
- audit mode to gather hashes of permitted programs.
- including remote locations for additional hash restrictions.
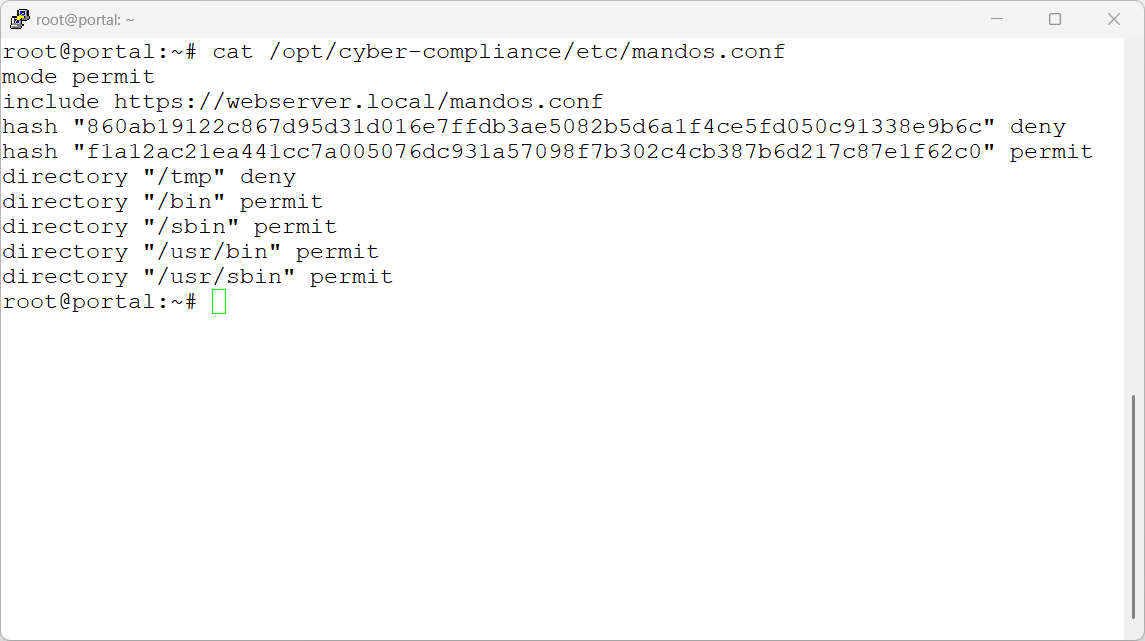
Deep Dive the Config File
What’s possible with minimal effort?
- Set a default mode. Anything not matched will have this action applied.
- Include a remote config file. If available, this adds to the local config rules.
- Hash identification of applications to “allow” and those to “deny”.
- Directories (and their sub-directories) to “allow” and those to “deny”.
All of these can be mixed and matched to get the desired state. All matches are logged to syslog.
Compliance Requirement
A common framework requirement is to limit which applications can execute. The reasoning is that if a malicious application can’t execute at all, the risk posed by that malware is reduced to near zero. An approach more reliable than malware protection. There are two approaches to this: whitelist or blacklist by directory, or whitelist by file-hash. mandos supports both methods simultaneously. The restrictions by directory have a lower administrative overhead while hash detection is highly accurate.
Prevent Privileged Users from Accessing the Internet – With vogan
- Choose who restrictions apply to
- Choose which networks to whitelist
- Manage locally or centrally
- Compliance within minutes
- Log all activity to syslog
Whitelist & Blacklist Applications & Directories – With mandos
- Choose which directories to blacklist and whitelist
- Choose which applications to blacklist and whitelist
- Combine directory rules, hash rules, and actions
- Manage locally or centrally
- Log all activity to syslog
Quick To Deploy to Small or Large Environments
- Register – Free trial for 14 days
- Download – Try on 5 Linux systems
- Configure – Sensible Defaults
- Apply – It’s that easy
Compliance Focused With Real World Benefits
- Frameworks – Results focused
- Effective – Easy to tweak settings
- Quick – Up and running in minutes
- Linux Focused – For Linux SysAdmins
Easy To Manage Licenses That Make Sense
- License – 1 seat per host, not per tool
- Seats – Movable between hosts
- Manage – Web portal management
- Sensible – Licenses that make sense
Your Data Remains In Your Region
Your data stays in your region of choice. That includes your Customer Portal, your license details, security and access logs, backups, and your centralised configuration management (if you’re using that feature).
