Get The Most From Your Redhat Linux Servers
AGIX Linux staff are experienced with all popular distributions of Linux. We work with Redhat Linux and those similar such as Fedora, CentOS and more.
Organizations typically decide on a single distribution to use within their business. When that distribution is Redhat, our staff are ready to help with a strong understanding of current best practices, strong training, and a history of hardening, supporting and maintaining Redhat Enterprise Linux systems.
See Our Blogs on Redhat, Fedora and CentOS Linux
Configure Metasploit with NMap and the Database – Advanced
All HowTo's
Cyber-Security
Linux
PostgreSQL
Redhat, Fedora and CentOS Linux
Ubuntu, Mint & Debian Linux
Web Servers
This article walks you through the process of installing, configuring and running scans using Metasploit and Nmap. Both CentOS 7 and Ubuntu 20.04 are discussed. Our objective is to be able to run nmap scans and have the results go into a database so we can filter the results later
Read More

Create Your Own Public Half-Life 2 DM Server on CentOS 7/8
All HowTo's
Linux
Redhat, Fedora and CentOS Linux
This article walks you through the process of building your own publicly accessible Half-Life 2 Death Match server on CentOS 7 and should work with 8 too but that’s untested. There’s plenty that can go wrong in this process. See the bottom of this article for common problems and solutions.
Read More

Fail2Ban with MySQL Database for IP Blacklisting
All HowTo's
Linux
MySQL & MariaDB
Redhat, Fedora and CentOS Linux
Ubuntu, Mint & Debian Linux
This article demonstrates how to configure Fail2Ban to use a MySQL (or MariaDB, etc) as the storage repository for IP blocking records. This allow multiple Fail2Ban services (running on multiple servers) to report and use a central IP blocking repository. A little context. In this article, we’re installing everything on
Read More

GeoBlocking with Apache on CentOS and Ubuntu
All HowTo's
Cyber-Security
Linux
Redhat, Fedora and CentOS Linux
Ubuntu, Mint & Debian Linux
Web Servers
This article describes how to protect your Apache web server by restricting which countries can access it. We’re using Apache on CentOS 7 but Ubuntu instructions are included and are very similar. I’ve given two examples; one on whitelisting everything except what we want to block, and blacklisting everything except
Read More

FreeRADIUS – Certificate Has Expired – Solution
All HowTo's
Cyber-Security
Linux
Redhat, Fedora and CentOS Linux
Ubuntu, Mint & Debian Linux
This article explains how to solve the issue of FreeRADIUS certificates expiring. In this example, we’re using CentOS 7 but the same should work on any Linux provided the paths are the same. The following commend errors due to a certificate expiring. systemctl restart freeradius SO we need to re-generate
Read More

Create Your Own Private Git Repo On Your Servers
All HowTo's
Linux
Redhat, Fedora and CentOS Linux
Ubuntu, Mint & Debian Linux
Your Git repo doesn’t need to be on Bitbucket or Github. You can very easily host a repository on your own systems. This article demonstrates this. We’re using CentOS here but any Linux OS should work. You just need the “git” package. As always, we’d love to read your comments.
Read More

Using Fail2Ban to Protect WordPress Logins (CentOS)
All HowTo's
Cyber-Security
Redhat, Fedora and CentOS Linux
Web Servers
This article demonstrates how to use Fail2Ban to block IP addresses attempting to compromise a WordPress instance via the login process. In this walk-through, we’re using CentOS 7 and FirewallD. Just be aware that if you’re using a caching service like CloudFlare, you can’t use this method because you’ll block
Read More
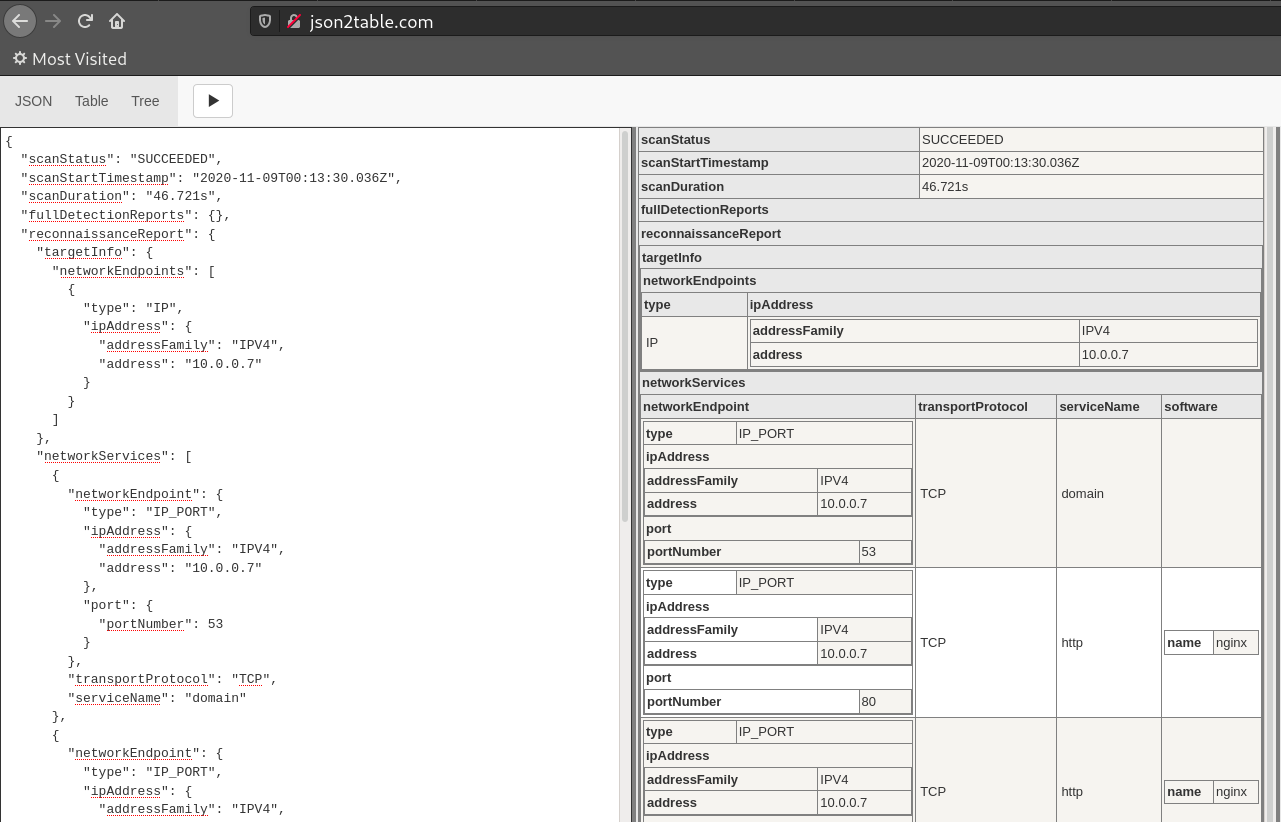
Installing the Tsunami Vulnerability Scanner on Fedora / CentOS 8
All HowTo's
Cyber-Security
Linux
Redhat, Fedora and CentOS Linux
This article demonstrates how to install the new Tsunami vulnerability scanner on a Redhat-like machine such as Fedora or CentOS 8 and how to use it including an example script to scan multiple targets or subnets. Install Java: yum install java-*-openjdk-devel Download the Tsunami ZIP from here: https://github.com/google/tsunami-security-scanner/archive/master.zip Extract the
Read More
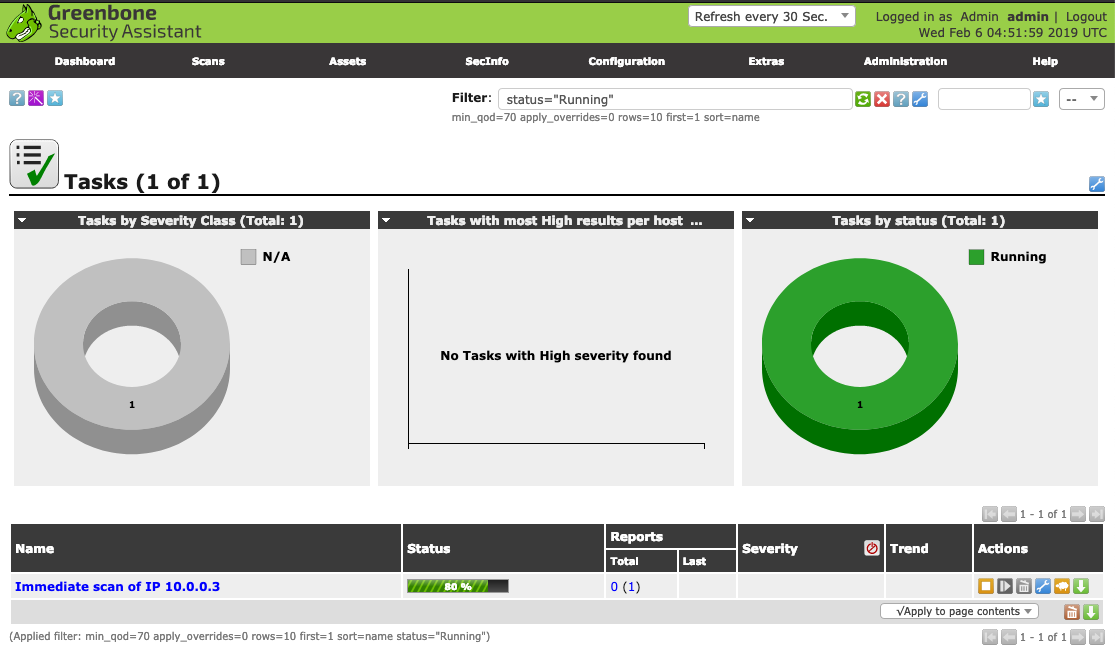
Installing OpenVAS on Kali in 2020
All HowTo's
Cyber-Security
Linux
Redhat, Fedora and CentOS Linux
Ubuntu, Mint & Debian Linux
This article explains how to install OpenVAS on Kali Linux. The difference between this method and others is the switch from “openvas” to “gvm” for naming/marketing. As you might have seen, I’ve written several articles on installing and using OpenVAS on CentOS. Don’t do it. Don’t go through the pain
Read More

Cracking WIFI with AirCrack-NG (Fedora, CentOS, RHEL)
All HowTo's
Cyber-Security
Linux
Redhat, Fedora and CentOS Linux
This article demonstrates how to crack a wireless network using the AirCrack-NG suite. Note that this will only work with WPA/WPA2 PSK wireless networks. That’s the limits of this generation of the AirCrack-NG suite. Only do this on a network that you own or are responsible for and have permission
Read More
Need Help?
Click Here

