All HowTo's
Get help with Linux, Automation, Cybersecurity and more. AGIX staff have the know-how and experience to help your organisation with best-practices, current technology in various Cloud environments including Amazon AWS. Our technicians support Ubuntu, Redhat, Databases, Firewalls, Ansible and Terraform, Storage and more.
This page shows examples of our work that AGIX shares freely with you. For a fully supported compute environment, contact our team to find out how we can help your organization move forward in the right way.
See Our Blogs on All HowTo's
Create, List, Copy and Delete Windows Shadow Copy (VSS) on Windows 10
All HowTo's
This article lists the PowerShell (and other) commands to create, list, copy from, and delete Windows Shadow Copies, also known as VSS. See Microsoft’s doco here “https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/vssadmin”. Enable: Enable-ComputerRestore -Drive "C:\" Create: wmic shadowcopy call create Volume="C:\" List: vssadmin list shadows Copy from: Windows Explorer: Right Click a folder, Select
Read More
Configure Metasploit with NMap and the Database – Advanced
All HowTo's
Cyber-Security
Linux
PostgreSQL
Redhat, Fedora and CentOS Linux
Ubuntu, Mint & Debian Linux
Web Servers
This article walks you through the process of installing, configuring and running scans using Metasploit and Nmap. Both CentOS 7 and Ubuntu 20.04 are discussed. Our objective is to be able to run nmap scans and have the results go into a database so we can filter the results later
Read More

Create Your Own Public Half-Life 2 DM Server on CentOS 7/8
All HowTo's
Linux
Redhat, Fedora and CentOS Linux
This article walks you through the process of building your own publicly accessible Half-Life 2 Death Match server on CentOS 7 and should work with 8 too but that’s untested. There’s plenty that can go wrong in this process. See the bottom of this article for common problems and solutions.
Read More
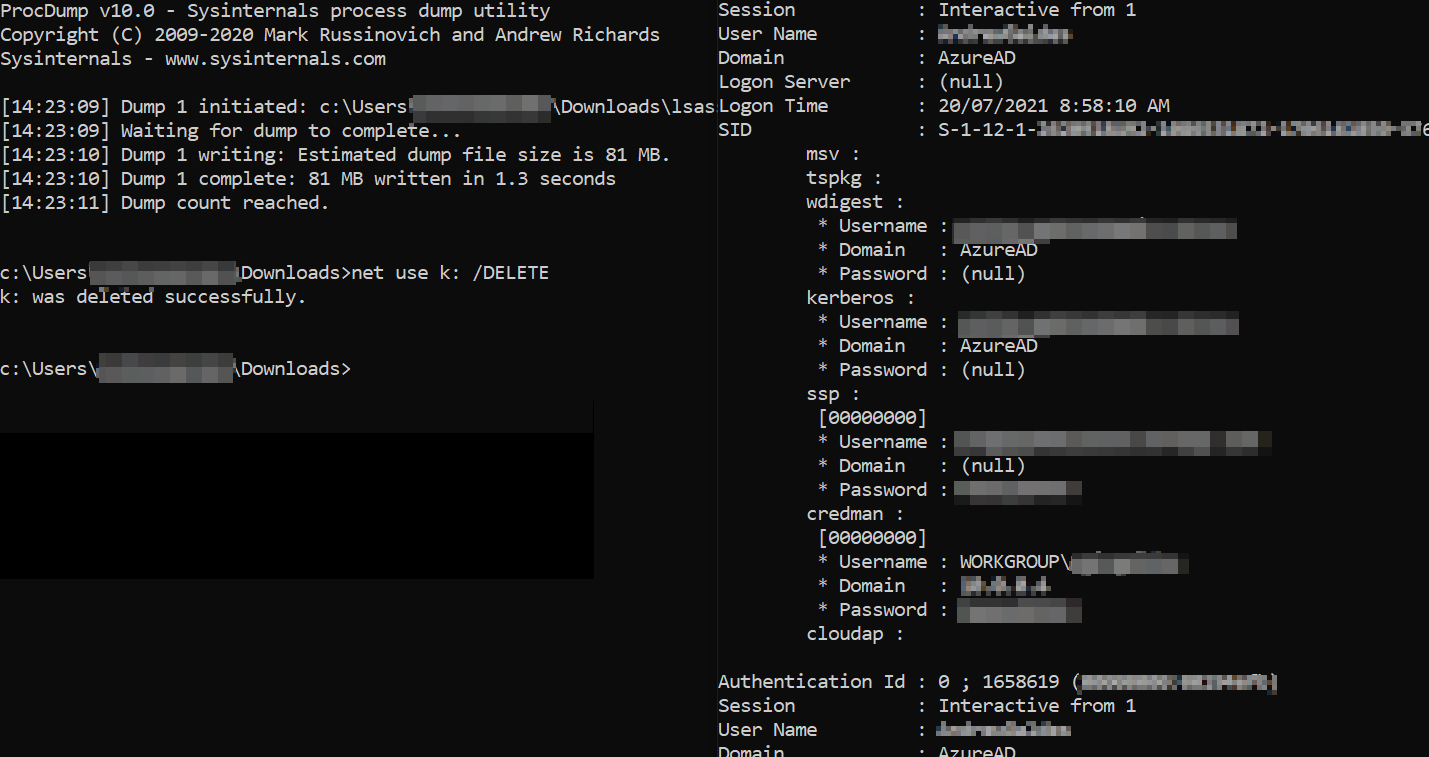
Get and Crack Windows Cached Credentials
All HowTo's
Cyber-Security
Windows
This article explains how to extract various Windows dumps of passwords from a target system. To follow along with this article, you’ll need to have administrative access to the target Windows machine, and any endpoint security will need to be tolerant of your activities. Any good AV will likely prevent
Read More
Windows 10 Post Install Setup
AGIX Discussion
All HowTo's
Windows
We don’t tend to install Windows very often these days. It seems to be far more stable than the old days and it mostly just works. But from time to time we do need to install it fresh and there’s a list of things we need to do to make
Read More

Synology High Disk Utilization – An Answer
All HowTo's
This article explains the primary reason for high disk utilization on the Synology NAS. In this example, we’re using the Synology DS720plus model. It has a 2 disk RAID1 configuration. The disks are 3.5 inch mechanical disks that honestly aren’t that great to begin with. Coupling that with the Synology
Read More

WiFi Penetration Testing with Ubuntu on USB Storage
All HowTo's
Cyber-Security
Linux
Ubuntu, Mint & Debian Linux
This article demonstrates how to use Ubuntu booted from a USB disk to do WIFI penetration testing. Why would you want to do this? If you have Windows on your laptop and need to use Aircrack-NG, you’ll need to fight with wireless adapter driver issues. So you’ll try Kali Linux
Read More

What you need in a Firewall
AGIX Discussion
All HowTo's
Cyber-Security
pfSense & Netgate
If you’re not filtering your internet traffic, you have a router, not a firewall. The good news is that most firewalls have features that can go a long way to protecting your IT and business resources. Let’s start with the different kinds of firewalls and their use-cases. A “packet filter”
Read More

Securely Wipe Disk and Try to Recover the Contents
All HowTo's
Cyber-Security
This article demonstrates how to securely delete files and all content from a disk, and then attempt to recover files form that disk. Warning: There is a risk you’ll make a mistake and wipe the wrong disk. So be careful. Identify the disk you want to work with: lsblk For
Read More
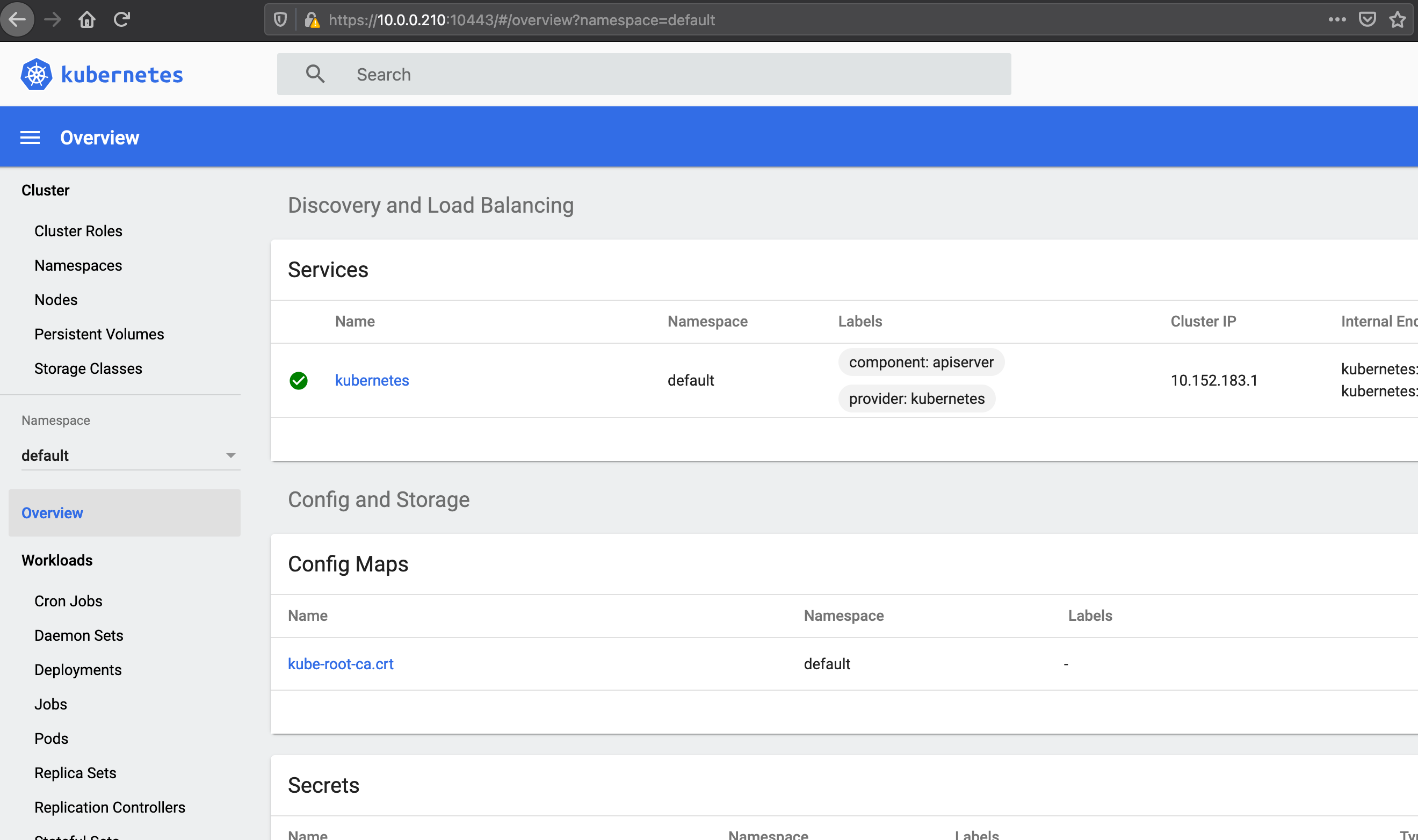
Kubernetes (MicroK8s) Part 4 – Microk8s in High Availability
All HowTo's
Kubernetes & Docker
The good news is that Microk8s can now be deployed in a multi-node architecture. And it’s simple to do. This video “https://www.youtube.com/watch?v=dNT5uEeJBSw” is a nice demonstration. It uses a floating IP between the cluster nodes that removes the need to use a load balancer in front of your cluster. Start
Read More
Need Help?
Click Here

